| Previous | Table of Contents | Next |
Type enforcement works by grouping all the processes into domains and types based on least privilege. Grouping by types organizes the files much like abstract data types. The type indicates how the data in the file were created and how they can be used. Then, a table, called a domain definition table (DDT), is defined to indicate how the process can access the files. Exhibit 1 shows an example of a type enforcement DDT. As shown in the sample DDT, the World Wide Web (WWW) server can only access Web files, and the mail system can only access mail files, such as the mailbox and mail alias files.

Exhibit 1. Type Enforcement Domain Definition Table (DDT)
Most systems allow processes to interact with each other directly via signaling or a more complex interprocess communication (IPC) mechanism, which must be controlled as well. In type enforcement, control is achieved by creating a table similar to the DDT called the domain interaction table (DIT), shown in Exhibit 2. In this example, the WWW is completely isolated, and the mail system and the word processor can communicate. Type enforcement involves defining the DDT and DIT such that the applications meet the least privilege requirement. Complete isolation is often not desirable, because applications must share data. Type enforcement allows the appropriate balance between least privilege and information sharing.

Exhibit 2. Type Enforcement Domain Interaction Table (DIT)
An important property of type enforcement is that the DDT and DIT tables cannot be modified while the system is running. This limitation stops attacks that modify data used for making security decisions. The static nature of type enforcement does not affect the usability of the system, because the type-enforcement tables describe only how the applications interact with data and each other. Thus, the type-enforcement tables change only if the way in which the applications interact changes.
Type enforcement partitions a system into a number of strong buckets. Each bucket has a domain and a list of all the types that that domain can access. The bucket also includes IPC channels to other processes in other buckets, as shown in Exhibit 3. Type enforcement provides a structure that separates applications and controls user access to applications. A file or application must be in a user’s domain for the user to access it. Users are allowed into a domain or bucket depending on their duties or roles on the system.
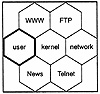
Exhibit 3. Type Enforcement Structure
Subsystem Separation
Now that a mechanism exists that closely matches the basic bucket principle, a variety of protection measures are possible. First and foremost, applications can be separated completely in different buckets, which ensures that two different applications do not interfere with each other. Type enforcement establishes the security level of separate computers while maintaining a linked system.
One possible security configuration that has been proposed to maintain Internet security is to have a different machine for each Internet service. The rationale behind this configuration is that many attacks over the network involve wedging open one service just enough to get a “toehold” on the system. From the toehold, the attacker expands his or her control by attacking the other Internet services in a sort of domino game. For example, a recently discovered Telnet vulnerability cannot be taken advantage of unless the attacker has write access to the system. If the site has an anonymous ftp site from which the attacker can download the key file, the system can be compromised. It is the combination of the two services that provides the vulnerability.
However, buying one machine for each Internet service is expensive. Type enforcement allows separate Internet services to be combined onto one system, on which each Internet service is placed in its own bucket. Thus, type enforcement prevents attacks that use combinations of Internet services.
| Previous | Table of Contents | Next |