| Previous | Table of Contents | Next |
Controlled System Calls
Type enforcement provides excellent separation at the file level. However, UNIX has many privileged system calls that allow users to access the kernel directly. Many system vulnerabilities result from malicious users employing system calls to compromise the system. Sidewinder solves this problem with a series of special flags for each domain, which indicate which system calls can be made from that domain.
For example, the is_admin flag is set only in domains that can be accessed by the administrator. This control allows the administrator to make system calls that no one else has the authorization to make. Note that these flags are part of the type enforcement information and cannot be modified while the system is running. Even root access will not allow a process to make disallowed calls. Untrusted users or software applications are placed in domains that do not have access to these powerful system calls.
Network Separation
Typically, firewalls have two separate physical network connections managed through a single protocol stack. Sidewinder has two separate network connections with two separate protocol stacks. This configuration allows Sidewinder to provide strong separation between data from the internal network and data from the external network.
If a firewall does not have network stack separation, network packets from both networks are processed by the same protocol engine. Exhibit 9 shows a system that does not separate data coming into the firewall. Software must be trusted to ensure that the origin of the packets is maintained correctly. The various pieces of data are all contained in the same information bucket. The protocol engine must also be trusted to detect an Internet system that is pretending to be a system from the internal side of the firewall.
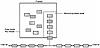
Exhibit 9. Firewall Without Network Stack Separation
Because Sidewinder has two network cards, it can always identify the origin of the information, no matter how clever the attack is. Information coming from the network cards is placed in separate domains. The information is kept separated until Sidewinder confirms that the information can move to the other domain. For example, the systems may be set up so that the administrator can telnet to Sidewinder from the internal side, but not from the Internet. Exhibit 10 shows the Sidewinder configuration in which two protocol stacks separate information coming from two networks. As a result, network protocol spoofing is not possible. As illustrated in this example, the information is kept in two separate information buckets. Only the proxy program can move data between the two domains.

Exhibit 10. Sidewinder Configuration
Protecting Internet Servers
The security features in Sidewinder can secure the Sendmail Internet server. Sendmail is the Internet server that runs on many UNIX platforms and listens for E-mail from the Internet. Sendmail is a complex piece of software and has been the source of numerous security vulnerabilities. These vulnerabilities allow hackers to compromise Sendmail, which then enables them to launch successful attacks on the rest of the system. MCI estimates that 20,000 systems were compromised through Sendmail over a one-year period.
Sidewinder protects the rest of the system by placing Sendmail in its own domain. From this domain, Sendmail can only access the network resources to get the mail from the Internet and to send the mail messages into the internal mail message queues. All the tools used by hackers are out of reach. Exhibit 11 shows the protected Sendmail configuration on Sidewinder which places it in a separate domain. This configuration also protects the system from illegal access through Sendmail, which is prevented from accessing the rest of the system.
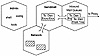
Exhibit 11. Secure Sendmail Configuration
A recent Sendmail vulnerability involved the syslog. Syslog is a system call that is used to write information to the audit log. However, syslog does not check to ensure that the size of the message that it is writing does not exceed the space available. The message to be appended to the log is stored on the programs stack. Thus, if a program allows users from the Internet to specify information to be logged, a hostile user can specify a long message that overwrites the programs stack. By placing executable code in the portion that is overwritten, the attacker gains complete control of the Sendmail program. This type of security violation has occurred. Attackers had an easy time of taking control of the Sendmail program and had Sendmail start up an interactive shell. From there, attackers used their Sendmail toehold to compromise the rest of the system.
On Sidewinder, the attack is stopped because Sendmail cannot execute an interactive shell. Even if a shell is running in the Sendmail domain, it could still not access the rest of the system. Thus, Sidewinder protects itself from Sendmail vulnerabilities that have not yet been discovered.
THE SIDEWINDER 2.0 CHALLENGE
Secure Computing has placed a Sidewinder on the Internet and challenged people to crack the system. The goal is to encourage sophisticated attacks on Sidewinder. Although Sidewinder has been tested thoroughly by trained engineers, field testing teaches more about how intruders attack systems. The goal of the challenge is to break through the firewall to the machine behind it. This machine contains a message signed with Secure Computing’s private key that can be used to prove that someone has broken through the Sidewinder firewall.
It was expected that someone would break through the earlier Sidewinder 1.0 challenge system, which took place during the early stages of development. After 1 year and 3500 visits from a variety of Internet users, no one was able to crack the 1.0 challenge. Due to the enhanced security in Sidewinder 2.0, the Sidewinder 2.0 challenge is expected to be much more difficult.
Challenge Site Information
Users who would like to try the Sidewinder challenge can find it at challenge.sidewinder.com, with IP address 206.145.0.254. There is a WWW server and an anonymous ftp server. As a reward, Secure Computing is offering a jacket with the Sidewinder logo on the back.
More information on the Sidewinder Challenge can be found at http://www.sctc.com. Users can also download a list of frequently asked Sidewinder questions by anonymous FTP from ftp://ftp.sctc.com/pub.
SUMMARY
The Internet servers running on the Sidewinder challenge have been protected using type enforcement. The Internet server applications are a combination of commercial and public domain software that have been integrated to provide current functionality with the best security. The success of the challenge shows that type enforcement has done exceptionally well in application.
| Previous | Table of Contents | Next |