| Previous | Table of Contents | Next |
Although no single Internet security control measure is perfect, one measure, the firewall, has in many respects proven more useful overall than most others. In the most elementary sense, a firewall is a security barrier between two networks that screens traffic coming in and out of the gate of one network to accept or reject connections and service requests according to a set of rules. If configured properly, it addresses a large number of threats that originate from outside a network without introducing any significant security liabilities. Because most organizations are unable to install every patch that CERT advisories describe, for example, these organizations can nevertheless protect hosts within their networks against external attacks that exploit these vulnerabilities by installing a firewall that prevents users external to the network from reaching the vulnerable programs in the first place. A more sophisticated firewall also controls how any connections between a host external to a network and an internal host occur. In addition, an effective firewall also hides information such as names and addresses of hosts within the network as well as the topology of the network it is employed to protect. Firewalls can defend against attacks on hosts (including spoofing attacks), applications protocols, and applications. In addition, firewalls provide a central way of not only administering security for a network, but also for logging incoming and outgoing traffic to allow accountability of user actions and for triggering incident response activity if unauthorized activity occurs.
Firewalls are typically placed at gateways to networks (see Exhibit 1), mainly to protect an internal network from threats originating from an external one (especially from the Internet). In this type of deployment the goal is to create a security perimeter (see Exhibit 1) protecting hosts within from attacks originating from external sources. This scheme is successful to the degree that the security perimeter is not accessible through unprotected avenues of access (Chapman and Zwicky, 1995; Cheswick and Bellovin, 1994). The firewall acts as a “choke” component for security purposes. Note that in Exhibit 1 routers are in front and in back of the firewall. The first (shown above the firewall) is an external router used to initially route incoming traffic, direct outgoing traffic to external networks, and broadcast information that enables other network routers as well as the router to the other side of the firewall to know how to reach it. The other router is an internal router that sends incoming packets to their destination within the internal network, directs outgoing packets to the external router, and broadcasts information concerning how to reach it to the internal network and the external router. This “belt and suspenders” configuration further boosts security by preventing broadcasting of information about the internal network outside of the network that the firewall protects. This information can help an attacker learn of IP addresses, subnets, servers, and other information useful in perpetrating attacks against the network. Hiding information about the internal network is much more difficult if the gate has only one router because this router is the external and internal one, and must thus broadcast information about the internal network to the outside.
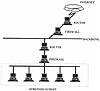
Exhibit 1. A Typicl Gate-Based Firewall Architecture
Another way that firewalls are deployed (although, unfortunately, not as frequently) is within an internal network — at the entrance to a subnet within a network — rather than at the gateway to the entire network (see Exhibit 2). The purpose is to segregate a subnetwork (a “screened subnet”) from the internal network at large — a very wise strategy when the subnet has higher security needs than those within the rest of the security perimeter. This type of deployment allows more careful control over access to data and services within a subnet than is otherwise allowed within the network. The gate-based firewall, for example, may allow FTP access to an internal network from external sources. If a subnet contains hosts that store information such as lease bid data or salary data, however, allowing FTP access to this subnet is less advisable. Setting up the subnet as a screened subnet could solve this problem and provide suitable security control — the internal firewall that provides security screening for the subnet could be configured to deny all FTP access, regardless of whether the access requests originated from outside or inside the network.
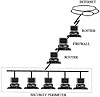
Exhibit 2. A Screened Subnet
Simply having a firewall, no matter how it is designed and implemented, however, does not necessarily do much good with respect to protecting against externally originated security threats. The benefits of firewalling depend to a large degree on the type of firewall used in addition to how it is deployed and maintained, as explained shortly. The next section of this chapter explains each of the basic types of firewalls and their advantages and disadvantages.
| Previous | Table of Contents | Next |