| Previous | Table of Contents | Next |
TRAPDOORS
Computer operating systems are designed to prevent unintended access to them and unauthorized insertion of modification of code. Programmers sometimes insert code that allows them to compromise these requirements during the debugging phases of program development and later during system maintenance and improvement. These facilities are referred to as trapdoors, which can be used for Trojan horse and direct attacks (e.g., false data entry).
Trapdoors are usually eliminated in the final editing, but sometimes they are overlooked or intentionally left in to facilitate future access and modification. In addition, some unscrupulous programmers introduce trapdoors to allow them to later compromise computer programs. Furthermore, designers or maintainers of large complex programs may also introduce trapdoors inadvertently through weaknesses in design logic.
Trapdoors may also be introduced in the electronic circuitry of computers. For example, not all of the combinations of codes may be assigned to instructions found in the computer and documented in the programming manuals. When these unspecified commands are used, the circuitry may cause the execution of unanticipated combinations of functions that allow the computer system to be compromised.
Typical known trapdoor flaws in computer programs include:
- • Implicit sharing of privileged data.
- • Asynchronous change between time of check and time of use.
- • Inadequate identification, verification, authentication, and authorization of tasks.
- • Embedded operating system parameters in application memory space.
- • Failure to remove debugging aids before production use begins.
- • Asynchronous change between time of check and time of use.
During the use and maintenance of computer programs and computer circuitry, ingenious programmers invariably discover some of these weaknesses and take advantage of them for useful and innocuous purposes. However, the trapdoors may be used for unauthorized, malicious purposes as well.
Functions that can be performed by computer programs and computers that are not in the specifications are often referred to as negative specifications. Designers and implementers struggle to make programs and computers function according to specifications and to prove that they do. They cannot practicably prove that a computer system does not perform functions it is not supposed to perform.
Research is continuing on a high priority basis to develop methods of proving the correctness of computer programs and computers according to complete and consistent specifications. However, commercially available computers and computer programs probably will not be proved correct for many years. Trapdoors continue to exist; therefore, computer systems are fundamentally insecure because their actions are not totally predictable.
Detecting Trapdoors
No direct technical method can be used to discover trapdoors. However, tests of varying degrees of complexity can be performed to discover hidden functions used for malicious purposes. The testing requires the expertise of systems programmers and knowledgeable applications programmers. Investigators should always seek out the most highly qualified experts for the particular computer system or computer application under suspicion.
The investigator should always assume that the computer system and computer programs are never sufficiently secure from intentional, technical compromise. However, these intentional acts usually require the expertise of only the technologists who have the skills, knowledge, and access to perpetrate them. Exhibit 9 lists the potential perpetrators, methods of detection, and sources of evidence of the abuse trapdoors.
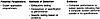
Exhibit 9. Detection of Trapdoors
LOGIC BOMBS
A logic bomb is a set of instructions in a computer program periodically executed in a computer system that determines conditions or states of the computer, facilitating the perpetration of an unauthorized, malicious act. In one case, for example, a payroll system programmer put a logic bomb in the personnel system so that if his name were ever removed from the personnel file, indicating termination of employment, secret code would cause the entire personnel file to be erased.
A logic bomb can be programmed to trigger an act based on any specified condition or data that may occur or be introduced. Logic bombs are usually placed in the computer system using the Trojan horse method. Methods of discovering logic bombs are the same as for Trojan horses. Exhibit 10 summarizes the potential perpetrators, methods of detection, and kinds of evidence of logic bombs.

Exhibit 10. Detection of Logic Bombs
ASYNCHRONOUS ATTACKS
Asynchronous attacks take advantage of the asynchronous functioning of a computer operating system. Most computer operating systems function asynchronously on the basis of the services that must be performed for the various computer programs executed in the computer system. For example, several jobs may simultaneously call for output reports to be produced. The operating system stores these requests and, as resources become available, performs them in the order in which resources are available to fit the request or according to an overriding priority scheme. Therefore, rather than executing requests in the order they are received, the system performs then asynchronously on the basis of the available resources.
Highly sophisticated methods can confuse the operating system to allow it to violate the isolation of one job from another. For example, in a large application program that runs for a long time, checkpoint/restarts are customary. These automatically allow the computer operator to set a switch manually to stop the program at a specified intermediate point and later restart it in an orderly manner without losing data.
| Previous | Table of Contents | Next |