| Previous | Table of Contents | Next |
The Escrowed Encryption Chips
The SKIPJACK algorithm and method that allows for government access are implemented in a tamper-resistant escrowed encryption chip that includes the following elements:
- • The SKIPJACK encryption algorithm.
- • An 80-bit family key (KF) that is common to all chips.
- • A chip unique identifier (UID).
- • An 80-bit chip unique key (KU), which is the XOR of two 80-bit chip unique key components (KUI and KU2)
- • Specialized control software.
- • An 80-bit family key (KF) that is common to all chips.
These elements are programmed onto the chip after it has been manufactured. Programming takes place inside a secure facility under the control of representatives from the two escrow agents. Batches of chips are programmed in a single session.
At the start of a programming session, the representatives of the escrow agents initialize the programmer by entering parameters (i.e., random numbers) into the device, as shown in Exhibit 5. For each chip, KU1 and KU2 are computed as a function of the initialization parameters plus the UID. The KU is formed as KU1 XOR KU2. The programmer places UID and KU onto the chip along with the chip-independent components.
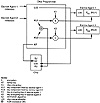
Exhibit 5. Chip Initialization
KU1 is then encrypted with a secret key encrypting key K1y assigned to escrow agent 1 to produce EK1(KU1), where EK(X) denotes the encryption of X with key (K). Similarly, KU2 is encrypted with a secret key K2 assigned to escrow agent 2 to produce EK2(KU2). The encrypted key components are each paired with the UID and given to their respective escrow agent to store in escrow. Because the key components are stored in encrypted form, they are not vulnerable to theft or unauthorized release.
At the end of the programming session, the programmer is cleared so that the KUs cannot be obtained or computed, except by obtaining their encrypted key components from both escrow agents and using a special government decrypt device. The first set of escrowed encryption chips was manufactured by VLSI Technology, Inc. and programmed by Mykotronx. Mykotronx’s MYK78 chip runs at about 15 Mb/s in electronic codebook mode.
Encrypting with an Escrowed Encryption Chip
For two persons to use the SKIPJACK algorithm to encrypt their communications, each must have a tamper-resistant security device that contains an escrowed encryption chip. The security device is responsible for implementing the protocols needed to establish the secure channel, including negotiation or distribution of the 80-bit secret session key (KS). The AT&T 3600 Telephone Security Device uses a proprietary, enhanced version of the Diffie-Hellman public-key distribution protocol for key negotiation. The device is placed between the handset and baseset of a telephone and activated with the push of a button.
Once an 80-bit KS is established for use with an escrowed encryption chip, it is passed to the chip, and an operation is invoked to generate a LEAF from the KS and an initialization vector (IV), which may be generated by the chip. The special control software encrypts KS using the KU and then concatenates the encrypted session key with the UID and an authenticator (A). All this is encrypted using the common KF to produce the LEAF. The IV and LEAF are then transmitted to the receiving chip for synchronization and LEAF validation. Once synchronized, the session key is used to encrypt and decrypt messages in both directions. For voice communications, the message stream is first digitized. Exhibit 6 shows the transmission of the LEAF and message stream “Hello” encrypted under KS from a sender’s security device to a receiver’s device. The diagram does not show the IV.
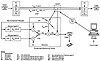
Exhibit 6. An Escrowed Encryption System
In a two-way conversation, such as a phone call, each party’s security device transmits an IV and a LEAF computed by the devices chip. However, both devices use the same KS to encrypt communications transmitted to the other party and to decrypt communications received from the other party.
| Previous | Table of Contents | Next |