- When is the division method of hashing a good choice?
- When is the middle square method of hashing a good choice?
LDL DLD
where L is always a letter (A-Z),
D is always a digit (0-9),
and is always a single space.
For example, the postal code for the
University of Waterloo is N2L 3G1.
Devise a suitable hash function for Canadian postal codes. ![]()
in the order given into a table of size M=16 that is initially empty. Use the following table of hash values:
| x | Hash(x) (octal) |
| "un" | 016456 |
| "deux" | 0145446470 |
| "trois" | 016563565063 |
| "quatre" | 010440656345 |
| "cinq" | 0142505761 |
| "six" | 01625070 |
| "sept" | 0162446164 |
| "huit" | 0151645064 |
| "neuf" | 0157446446 |
| "dix" | 01455070 |
| "onze" | 0156577345 |
| "douze" | 014556647345 |
-
Rewrite the insert method so that it doubles
the length of the array when
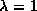 .
. -
Rewrite the withdraw method so that it halves
the length of the array when
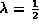 .
. - Show that the average time for both insert and withdraw operations is still O(1).
- Devise an algorithm that uses a hash table to test whether S is a subset of T. What is the average running time of your algorithm?
-
Two sets are equivalent
if and only if both
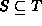 and
and 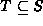 .
Show that we can test if two sets of integers are equivalent
in O(m+n) time (on average).
.
Show that we can test if two sets of integers are equivalent
in O(m+n) time (on average).
- What are the worst-case running times for insert, find, and withdraw.
- What are the average running times for insert, find, and withdraw.
![]()
where c(i) is a full-period pseudo random number generator. Why is such a sequence likely to be better than either linear probing or quadratic probing?